Azure Monitor Agent VM extension with Terraform
Logging requirement is part of good practice and security frameworks like ISO and NIST. It is desirable to implement it from day one into your architecture. Microsoft offers a Log Analytics Workspace where you can store logs and virtual machine extensions to send data from a guest operating system, like performance metrics and system events (Windows or Linux). The Log Analytic Agent we used in the past won’t be supported as of 2024-08-31. In this post, I will demonstrate how to install and configure a successor, Azure Monitor Agent (AMA) on Windows virtual machine to send logs to Log Analytics workspace using Terraform. In our scenario, we will collect Windows Events and save them to the Log Analytic Workspace. To achieve it we will need the following items in our lab environment.
- Log Analytics workspace
- VM extension
- Data collection rule
The Terraform code is available in DBAinTheCloud GitHub repository.
Log analytic workspace
For the demo environment, we have created a basic Log Analytics workspace with the basic specs (sku and retention).
resource "azurerm_log_analytics_workspace" "logging_ws" {
name = join("-", [local.prefix, "la1"])
location = azurerm_resource_group.rg1.location
resource_group_name = azurerm_resource_group.rg1.name
sku = "PerGB2018"
retention_in_days = 30
}
VM extension
Configuration of VM extension in default configuration is straightforward. In this setup, we are using system-assigned identity for VM however user-assigned identity is supported and recommended for large-scale deployments.
resource "azurerm_virtual_machine_extension" "ama" {
count = var.server_count
name = join("-", [local.prefix, count.index + 1, "ama"])
virtual_machine_id = element(module.vm-win.vm_id, count.index)
publisher = "Microsoft.Azure.Monitor"
type = "AzureMonitorWindowsAgent"
type_handler_version = "1.10"
auto_upgrade_minor_version = "true"
depends_on = [module.vm-win, azurerm_log_analytics_workspace.logging_ws]
tags = merge(var.tags, tomap({ "firstapply" = timestamp() }))
lifecycle {
ignore_changes = [tags]
}
}

Data collection rule
The data collection rule is a new object and it is a replacement for the Legacy agents management section from log Analytics used for the management of Log Analytic agents. It contains two configuration sections.
- Data sources - entire data flow, what logs we are collecting and where we are sending it.
- Resources - link to the VM we are monitoring
resource "azurerm_monitor_data_collection_rule" "rule1" {
name = join("-", [local.prefix, "rule1"])
location = azurerm_resource_group.rg1.location
resource_group_name = azurerm_resource_group.rg1.name
depends_on = [azurerm_virtual_machine_extension.ama]
destinations {
log_analytics {
workspace_resource_id = azurerm_log_analytics_workspace.logging_ws.id
name = "log-analytics"
}
}
data_flow {
streams = ["Microsoft-Event"]
destinations = ["log-analytics"]
}
data_sources {
windows_event_log {
streams = ["Microsoft-Event"]
x_path_queries = ["Application!*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0 or Level=5)]]",
"Security!*[System[(band(Keywords,13510798882111488))]]",
"System!*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0 or Level=5)]]"]
name = "eventLogsDataSource"
}
}
}
# data collection rule association
resource "azurerm_monitor_data_collection_rule_association" "dcra1" {
count = var.server_count
name = join("-", [local.prefix, count.index + 1, "dcra"])
target_resource_id = element(module.vm-win.vm_id, count.index)
data_collection_rule_id = azurerm_monitor_data_collection_rule.rule1.id
}
Data Sources - Data source

Data Sources - Destination

Resources

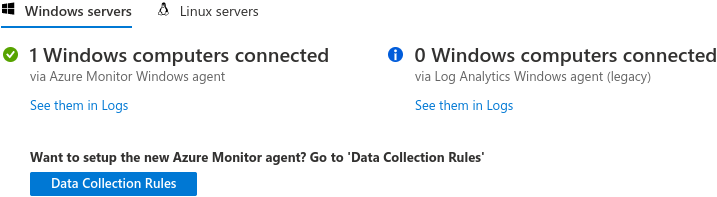
Congratulation!
After a successful deployment, we will see Windows events in the Log Analytics Event table.

If you need help with implementing a DevSecOps program and adding a security twist to your DevOps CI/CD pipelines get in touch.